Why Does Active Directory Matter?
 It still causes me uncomfortable dispepsia to admit that Microsoft’s directory coup worked so well. Since Windows desktop systems are so challenging to own without it, Microsoft succeeded at pushing Active Directory into wide deployment in the business world. As advocates for desktop Linux promote fitness and readiness for use in the business world, few seem to surmise what a strong fortress Microsoft has built around Windows. It’s not just about the platform; the enterprise infrastructure matters, too. When it comes to business information technology, the subtext beneath “just replace the desktops of the types of user for whom Linux is ready” reads “change your management system for all these user’s desktops, too.” Such a proposition is unsavory to the already change-averse IT culture.
It still causes me uncomfortable dispepsia to admit that Microsoft’s directory coup worked so well. Since Windows desktop systems are so challenging to own without it, Microsoft succeeded at pushing Active Directory into wide deployment in the business world. As advocates for desktop Linux promote fitness and readiness for use in the business world, few seem to surmise what a strong fortress Microsoft has built around Windows. It’s not just about the platform; the enterprise infrastructure matters, too. When it comes to business information technology, the subtext beneath “just replace the desktops of the types of user for whom Linux is ready” reads “change your management system for all these user’s desktops, too.” Such a proposition is unsavory to the already change-averse IT culture.
What does Active Directory for Windows desktops? For brevity’s sake, let me risk over-summarizing. (I’ll suffer corrections in comments on this post.) Active Directory is more than mere authentication for users. It represents desktop systems as known objects for increased security and management purposes. For laptops (which I generalize here as a type of desktop), it provisions user accounts to locally for offline use. It provides basic application deployment, standardizes system configurations, and locks down user interfaces through Group Policy Objects. Lastly, it issues Kerberos tickets to enable single sign-on to enterprise applications.
So, what’s the net for desktop Linux in the business world? Essentially it’s that any benefits that Linux desktops might provide in lowered licensing costs, increasing security, and so on, are quickly offset if it means bucking the established security and management model. Businesses that use Active Directory for managing Windows desktop systems–and there are a lot of them–don’t have to be Microsoft adherents to resist adopting desktop Linux desktop.
Samba and SUSE Linux Enterprise Desktop
A lot of thinking and research went into the creation of SUSE Linux Enterprise Desktop in order to ensure that it could penetrate the Active Directory fortress and provide real business value. SUSE engineers Guenther Deschner and Lars Mueller focused intensely (over 14K lines of code) on adding Active Directory capabilities into Samba.
Here’s the short list of what they made accomplished, all with no configuration changes required to the Active Directory system:
- Linux desktops can join Active Directory, becoming actual objects within an Active Directory domain (as workstation objects)
- Users can authenticate using their Active Directory credentials
- Proper interfaces present to the user according to Active Directory password policy (such as password has expired, do you want to change, and failed attempt due to login time restrictions)
- Account credentials are securely cached for offline use (a requirement for mobile users)
- Active Directory-based single sign-on works (Kerberos tickets are requested, renewed and refreshed automatically)
Again I summarize, and perhaps too much. For a more thorough and adept introduction, Novell Open Audio presents an interview with Lars Mueller.
Supplementary Screen Shots
To augment and illuminate Lars’ just-released Novell Open Audio interview, here are some screenshots Lars and I did together while at the SUSE Labs Conference in the Czech Republic.
Installation
Installation Change for Better Networking
One of the base changes to installing SUSE Linux is that the installer no longer uses the generic default system name of “LINUX.” Instead, the installer appends a random four-character string to each machine name. Although the team originally implemented this to avoid naming conflicts when joining Active Directory, it is very helpful in Dynamic DNS and simple WINS environments, too.
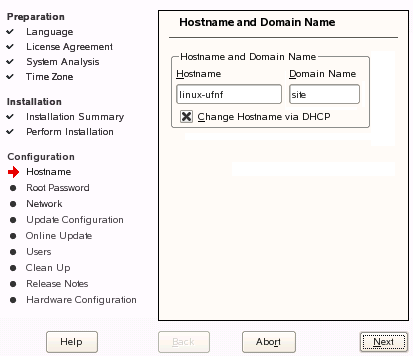
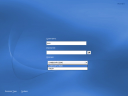
Defining the Authentication Source During Install
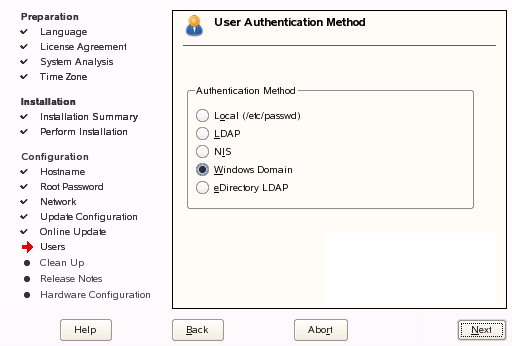
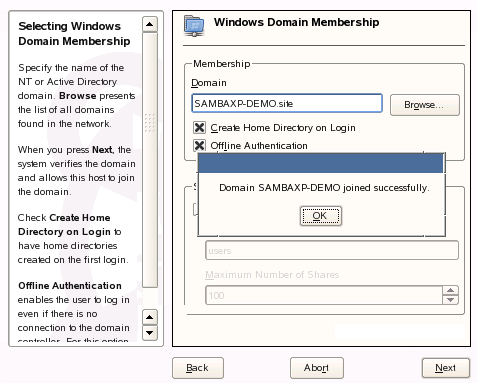
At the end of the SLED10 installation process, you can define the install source as “Windows Domain” in order to join an Active Directory Domain.Install: Specifying the Which Domain
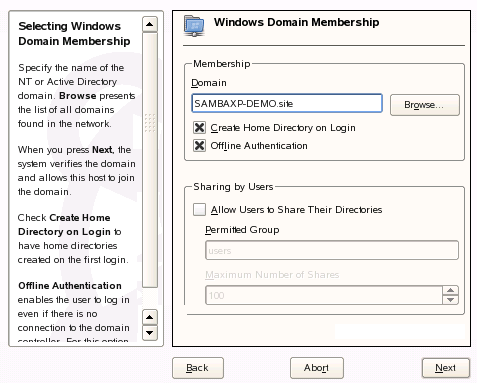
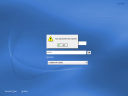
If you choose to use a Windows Domain as the workstation’s install source, you will need to specify which domain to join. This interface is also where you specify whether to create a local home directory when a local user is created from the Active Directory domain, as well as whether to allow the locally-created user account to authenticate when the domain cannot be reached.Install: Authorizing the Domain Join
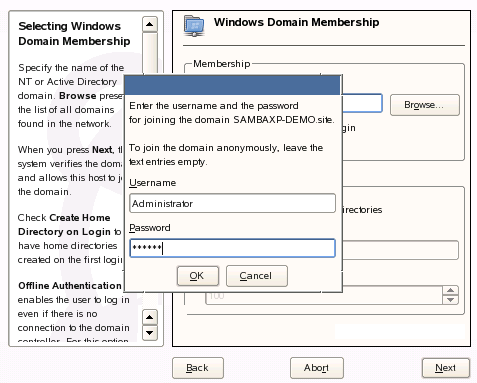
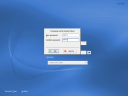
Of course, in order to join the domain and create the workstation object, you need to authenticate using an Active Directory user account that has appropriate permissions.Install: Confirmation for Successful Domain Join
It’s always nice to know whether something has worked.SLED10 System Viewed in the Microsoft Management Console
It’s always nice to know whether something has worked. So here are thumbnails of the MMC interface before and after the above process has been done, showing that the workstation object has been created in the domain.
Options for Already-Installed System
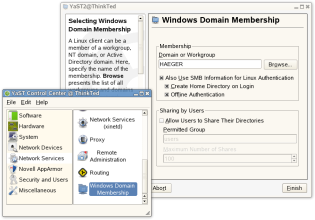
Enabling Through YaST on an Already-Installed System
This the management console interface for configuring a SLED10 workstation to use Active Directory for authentication. In it, you can see where to configure the AD domain name, whether to create a home directory on the server, and whether to cache credentials for offline use. Next steps after this one are the same in the installation steps shown above. (Click the image to embiggen.)
What the User Sees
The SLED10 Login Interface for Active Directory
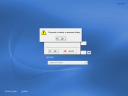
When a user wants to log in to her workstation, she has a new “Domain” option. We show it here with the Domain drop-down activated so you can see where other Active Directory domains would show up, as well as how a user can select <local> for offline or local (/etc/passwd) accounts. This screenshot shows KDE’s login interface (kdm). Gnome’s is very similar. (click the image to embiggen)Change Password at Login
If the user account setting is flagged “Change Password at Next Login,” the user will be prompted with an appropriate interfaces.Kerberos Ticket Example
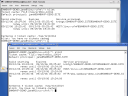
Service Ticket
Part of logging on to Active Directory includes the issue of a Ticket Granting Ticket, or TGT, for the user’s login session. The TGT essentially does what it’s name implies: it’s a Kerberos ticket used to request other types of Kerberos tickets, primarily Service Tickets. When you have a valid TGT and try to access a Kerberized service, which includes most *NIX-hosted applications and, more recently, most Windows Server applications that use Active Directory. This is how enterprise single sign-on is enabled for Windows clients–an advantage that few Linux advocates understand Windows has traditionally held over Linux on the business desktop.The utility klist provides a quick look at the Kerberos ticket cache on a linux system. In the screenshot below, the console window in the back shows that we used klist to show our current tickets, including the TGT (listed as “krbtgt”) and our host ticket. There are no Service Tickets in the cache. We then used Firefox to open Outlook Web Access, which did not prompt us to log on because the Active Directory-based Kerberos system allowed the workstation to request and receive the Service Ticket for Outlook WebAccess. This is shown in the console window in the front as the new HTTP item in the klist output.
If you find this article interesting, please Digg it.
Addenda:
- Steven J. Vaughan-Nichols adds some good details in his related article
- Ireland’s Jorge O’Castro weighs in regarding relevance to Ubuntu
- Gizbuzz has posted the first SLED10 review that mentions AD integration
- Hay un pequeno version in espanol
- Et il y’a une petite version en francais, aussi
Read of my articles on desktop Linux advocacy and execution.
Filed under: Advocacy, Free Software, Novell | Tagged: active directory, Group Policy Objects, kerberos, Linux, Novell, samba, SUSE Labs, windows, WINS |








Nice, thorough treatment.
So how do you join a domain with another distro, like Ubuntu or FC?
Chris (2):
Since all this code has been done as part of the Samba project, there are two ways to get this working on other distros:
Find out whether/when the distro vendor intends to integrate it.
Pull down changes from source code. I am not sure whether the sources have been accepted upstream yet, but I am confident that they will since Lars and Guenther work with Jeremy Allison here at Novell.
Since most distributions do not focus as much on integrating with enterprise infrastructure, they may not enable these features because of the extra testing effort it would take them. So, it’s still to be seen.
–T
Just a quick note: You’re absolutely right Ted, all our changes to the Samba tree are committed upstream.
Guenther
The code is already in upstream. It’s actually developed there and ported into SLES/SLED. It takes a lot of work to test all this though so I’m not suprised no one else has done this yet.
Jeremy.
Chris (2): From the command line you have to use the net command which is provided by Samba. Most current Linux versions include this program in the samba-client package.
How does one do a mixed authentication thing where there are Linux users and Active Directory users? The install seems to offer either, not both.
Roger (7):
According to Lars, you can have local user accounts and Active Directory accounts on a single machine. They are additive. Perhaps Lars will comment further on this.
–T
Nice, Ted, except you missed one major feature in Active Directory, incidentally the one feature that Samba seems to be lacking altogether: roaming profiles.
For the (luckily) uninformed, roaming profiles allow user Joe to login to an AD computer ‘Joes-pc’ PC, and synchronize the contents of his Profile (the equivalent of his home directory) with a copy on a file server. When X logs out, any changes to his Profile will be populated out to the server copy. As a result, Joe can log into any AD-enabled PC in his AD domain, and have his documents, desktop settings, application behavior, etc., avaialble to him. Since it is stored locally on each machine, should he have to go offline, his profile can go with him.
Although similar behavior can be created by mapping in a network share, that doesn’t provide the redundancy, offline capacity, or a similar experience to the roaming profile in Windows.
As soon as my home folder starts following me around my office, from Linux box to Windows box to Linux box, my users won’t have any reason to not run Linux clients in an Active Directory domain. Until then… I wait.
I am new to this, I am looking for Ubuntu 6.06LTS to integrate with Active Directory for a pending project. If anyone has done this successfully I need their expertise ASAP. If I am not breaking any rules I can be reached 24 hrs\day at XXX-XXX-XXX
Vincent Stewart Chicago, IL
[Note from Ted: Vince: I removed the phone number because I really don’t want my blog to become a place where phone numbers are permanently recorded. If you want to use Ubuntu for this, the Ubuntu Forums are the right venue for making contacts and getting help. Ubuntu users are generally very helpful. If you would like to try out SLED fo this, I have contacts in the Chicago area. –T]
Roger (7): It’s possible to mix different authentication sources. For example local, LDAP, and MS AD users.
You see this in the first displaymanager screen shot. There we have ‘local’ which results in not adding anything in front of the username.
While any selected domainname will end in ‘domainname\username’ as the resulting username. You see this e.g. in the shell prompt of the last screenshot with the two terminals.
bear454 (9): The roaming profiles are on our todo list.
For the authentication we already have the offline feature.
And I hope you do not have to wait to long to see a solution like roaming profiles provided to Microsoft Windows systems.
Also, if you’d prefer to have your local Linux username be the same as your AD username (without the added domain\username syntax, add into your /etc/samba/smb.conf file the following directive:
winbind use default domain = yes
and then also change the line
template homedir = /home/%D/%U
and remove the %D out of that to prevent the home directory from also having the domain component in it. This is assuming you are using pam_mkhomedir in your pam stack (to automatically create a local home directory on the users workstation when they log in).
[…] In a recent episode of Novell Open Audio (the Novell user’s podcast), host Ted Haeger discussed SLED’s Active Directory integration and apparently it is possible to login via Active Directory, be managed within Active Directory and more. Unfortunately, again I don’t have the ability to test this functionality myself, but apparently the AD integration is getting better all the time and using SLED10 within a ‘Windows shop’ is, according to Novell, a lot more of a oractical solution than it used to be. […]
Somebody knows if Red Hat or Fedora already can do this too???
Is there any work being done to translate and integrate AD group policy into the Suse envireonment? Is there any standards effort in this direction? http://www.css.taylor.edu/~nehresma/samba.html
indicates that something workable can be achieved. Is Novell woking with GPTF.org (Group Policy Task Force) in this area? Does anyone have any comments on the commercial commercial product “Centrify”?
Robert (16):
GPO’s are extremly Windows-specific, and the way they are applied in Active Directory has flexibility issues for really good administration. Personally, I don’t think the effort would be worth it. But, my opinion does not mean that someone will not try. Regarding GPTF.org, the question is whether the Samba guys are working on that or not. As with the work Lars and Guenther (from Novell) did, the effort needs to be lead by the open source project.
I know the CTO of Centrify. It looks like a cool product to me, particularly for migrating user profiles from Windows to Linux. It’s on my to-do list of things to cover (eventually) on Novell Open Audio.
–Ted
How do you cache credentials and network information for offline authentication? I have been using pam_ccreds to cache authentication information. This works well. I have also been using nscd to cache network information (i.e., UID -> username), but this does not work as well.
See http://www.flyn.org/laptopldap/laptopldap.html, especially “Issues.”
the_archer, I have been able to use Linux systems in an Active Directory environment since FC3. The measure of ‘success’ varies, also because our environment is among the worst of worst case scenarios.
For password authentication, system-config-authentication should be able to set up an appropriate krb5.conf for you (we don’t do that, because our AD deployment is trickier than average, starting from the disjoint namespace). For user information (real name, shell, etc.) we use a local LDAP server, because 1) I am not an AD administrator and never will be made so (in a catastrophic scenario, it could literally be a matter of life and death) 2) there’s tens of thousands of users in our AD deployment, but our group only needs to deal with a few tens of them. Samba’s winbindd should be able to handle user information without a local LDAP server, if you have no special needs.
As for joining the domain, we had a harder time than usual there, too. As I said, we are not AD administrators. Samba’s net command should be able to join machines even with AD users that have only the ‘can add machines to the domain’ attribute, but as of recent versions of Samba that does not work yet (it does from a Windows box). Our workaround was for the AD guys to create a separate OU for our group and give us complete control over it. Since then, we have been able to add to use the net command to add machines. It looks like the Novell UI wouldn’t help us there, because it seems to use the default OU only (hint, hint).
Keytabs have been a pain, too. You can get an HTTP service principal and successfully have Apache authenticate users without entering passwords (IE works out of the box, Firefox needs SPNEGO to be enabled). Getting principals through Samba for services other than Windows’ list of default ones (e.g. nfs, if you want to try kerberized nfsv4) is still broken.
For offline authentication, pam_ccreds seems to finally work. Support for it in system-config-authentication hasn’t been completed yet, so you’ll have to edit your PAM files manually for the time being.
Nice to see Novell concentrating on this aspect of the desktop. I agree that microsoft have created a fairly inpenatrable fortress of windows with AD. Here are my thoughts;
Microsoft’s implementation of kerberos causes lots of issues which makes SSO difficult in some situations. i.e. SPNEGO through a web browser to an apache server running on a linux box, authenticating with a windows krb server. There are a few things which need to be worked on regarding this and some of that is related to putting together a resonably fault tollerant and microsoft tollerant krb5-ws pam_auth_kerb for login and mod_auth_kerb for apache, better keytab management and more. I did do a lot of work on this in the past but without the time to dedicate to it I can’t really do much about it myself.
Sabayon is great, and it would be brilliant if sabayon could work with the microsoft group policy manager. Moreover it would be good if openldap/Fedora Directory Server/eDirectory could perform the same kind of policy deployment capability for windows _AND_ linux clients.
Integrating SElinux with OpenLDAP or AD or eDirectory would also be a good idea, having UNIX systems respect the permissions the server dishes out with effective permissions and heirarchical permissions which follow an organisational chart would push linux higher up the food chain with governments and large organisations, heck we’ve already got them beaten to a pulp over viruses and malware.
Policies & permissions are one of the most important parts of AD/windows server in large setups.
Directory oriented printer management would rock, in both ways, for instance being able to browse an AD servers printer list in the printer configuration in redhat/suse/ubuntu, and also being able to browse an openLDAP/FDS/eD printer list in the printer configuration of redhat/suse/ubuntu/windows/OSX.
We still need to think about software deployment in linux, if an openLDAP/FDS/eD and related errata type setup could deploy to windows clients and a similar and possibly syncronous yum/zen/apt/emerge/wine-doors type deployment architechture could be considered. It would have to be fairly polymorphic with respect to the install/update managers as there are lots of them around (plugins anyone?).
As brushed upon software deployment could also be tied in with wine, hopefully soon wine-doors will offer enough in the way of functionality to start work on this kind of architechture for wine on linux/OSX.
Exchange is monolithic and thats bad. An exchange to caldav conversion service would be nice. Especially so it could be poked out over the internet through a firewall, I don’t know about others but I’m not confident that exchange should go anywhere near the internet as security is such a major issue.
And finally, we need something for directory management in the way of a GUI which isn’t horrible (FDS), web based (phpldapadmin), has the same kind of features as FDS, eDirectory. Preferably for gnome, python is a good candidate for this.
BTW: Novell, rev. Ted, open source eDirectory 😉
bear454, I’ve done roaming profiles in samba for windows clients before, this may get you started; http://daniel.fiser.cz/?go=samba
The profile gets pulled to the client just as it would using a windows PDC. You can’t BDC a windows PDC with samba as yet, that seems to be the next big leap with regard to roaming profiles.
It would be nice if roaming profiles were respected by linux clients though. Having a linux client pull a profile would be a great achievement. You can of course mount the profile in linux or connect to it through gnome, and with pam_keyring or pam_auth_krb it works reasonably well.
Me thinks having Group Policy is just as critical for the success of Linux desktop as getting AD authentication to work, ie how will you manage 1000s of Linux workstations that no doubt will be deployed in a mixed environment of Macs and Windows systems. So it sounds like from post 17 we will have to rely on Centrify’s solution (www.centrify.com) that offers AD authentication and GP for *nix solution, which is fine as it sounds like a good solution …
How do you handle UID/GID mapping consistently between different Linux machines? In our case we have centralized home directories via NetApp filers, and having consistent UIDusername mapping is essential.
For consistent UID/GID mapping, I’d love to see Apple’s solution implemented in winbind (well, idmap).
They use the first 31 bits of the user/group objectGUID as the uid/gid.
Their directoryservices AD plugin looks up groups and users by CN though, and then gets confused when more than one of the same name turn up in your domain. I *think* winbind uses the sAMAccountName instead, which is guaranteed to be unique across a domain (or broken in the domain if not).
Joe (23): For a Linux desktop system there is no need to have a UID/ GID mapping from Microsoft to the Linux world. As soon as data is transfered from one system to another by network the data beongs to the right user. No matter which numeric ID is assigned.
In general it’s possible to have a central UID/ GID mapping with the help of ‘idmap backend = idmap_ad’ for example. See Samba’s smb.conf man page for more alternatives regarding the centralised idmap options.
As for offline login, winbindd does it’s own caching of credentials to allow offline login, and will re-establish krb5 credentials on network re-connection. It’s kind of becoming the LSA of the Linux world (sorry for the Windows joke there :-).
For Firefox/IIS server integration there’s a patch to firefix we use that uses ntlm_auth (part of Samba) to get the cached credentials to provide a single-sign on environment with Windows web servers. Works really well.
Jeremy.
You’re absolutely right, Ted.
Using N bits of the objectGUID as the UID/GID is a really bad idea because there is no guarantee that the N bits will be unique. A GUID is only unique for all 128 bits.
Ok…So how does Novell plan to handle domain policies? I have seen it mentioned many places but no one has answered any queries. Some of the big features introduced with AD 2003 and XP were windows firewall and the ability to remotely configure it and Remote Desktop/Remote Assistance with integration through messenger. There are many more important features but the little things make the mortar between the bricks in this impenetrable fortress. With AD 2003/XP I can seamlessly and remotely open port 3389 to a specific IP address or subnet, enable remote assistance and the user can simply run a gpupdate /force and then invite me to help them through windows messenger giving me a TS session to their desktop. I can also, with a simple domain policy push out a list of shared favorites and shortcuts based on OU and never have to worry about roaming profiles to support it. I would love to drop Windows tomorrow but in our 6000 device world I just can’t support them. Even with tools like Altiris, it is still a dream, because most tools only marginally support *NIX OS’s. If anyone has heard of any move to embrace domain policies I would love to hear about them!
[…] Can Linux Desktops Live in an Active Directory World? « Open Source Advocacy with Reverend Ted […]
This is a great step forward for Linux integration into a Windows AD network. I’m wondering however if the pass-through authentication demonstrated with Firefox and Outlook web access required modification to Firefox as well ? Can Firefox for Win32 do this as well and How ?
Nice article, I am using this feature on SLED on regular basis.
What is bad is narrow impact of this logon type in linux. It should work same way as it works in windows, where every program running, every application uses context of current credentials.
For example: why do I have to write my password once again in Evolution? In Firefox? etc etc…
enki (32):
Firefox should get a kerberos ticket for any kerberos apps. Evolution is probably kerberized, too. Is your Active Directory system issuing kerberos tickets?
–T
[…] estações Linux ao Active Directory “Ted Haeger mostra em seu blog como configurar o Suse para integrar-se em um ambiente Active Directory, enquanto Lars […]
COOL! I will try that!
[…] Ted Haeger goes on to show how Linux desktops are now integrating into Active Directory more and more seamlessly, with less and less work on the admin side. It used to be that you had to edit your PAM stack, tweak LDAP lookups, mess about with Kerberos and the like. Now it all works through a nice GUI at setup. What more could you ask for. […]
How will the linux client mount the home directory after authenication against AD occurs? We’re assuming the home directories are on a windows server?
Yasi [37]:
With Samba, the home directories can be hosted on any server platform that Samba runs on, or it can be a Windows server.
However, that does not mean that mounting or mapping a home folder is included for Linux systems. From what I remember, it is not, so you would need to script the mount to make it happen.
–Ted
[…] Haeger mostra em seu blog como configurar o Suse para integrar-se em um ambiente Active Directory, enquanto Lars […]
This is works well in SUSE Linux 10.2 too…
but how to share folder to some users from ADS???
i’ve doesn’t found an answer in internet….
WOW thank you for the detailed explanation with screenshots.
Computer.Pers [40]:
If you are asking about sharing out from a local workstation, then I do not know the answer on it. Sorry.
–Ted
how i can join Redhat desktop to Active directory
@ashraf [43]:
Red Hat Desktop should include a recent enough version of Samba, so the mechanism will be similar. You may need to edit samba config files, or perhaps Anaconda offers a config option for this. I do not use Red Hat, so you will need to consult documentation from Red Hat.
–T
Hi all, nice article, but have a cuestion about authentication, is it possible to keep the AD login in SLED 10 SP1 so Firefox can automatically login into an ISA Server Proxy? Anytime any user open up Firefox they must write their credentials again…
Regards
A good resource for Linux living in AD world. In case someone still feels at sea when it comes to AD please visit http://activedirectoryfaq.blogspot.com
[…] do with how well Windows works with their current infrastructure. But now Linux can play, too…read more | digg […]
[…] read more | digg story […]
[…] do with how well Windows works with their current infrastructure. But now Linux can play, too…read more | digg story Posted in Uncategorized RSS 2.0 | Trackback | […]
Thanks for this very good article.
So, Linux work is going slowly integrates in AD.
with Samba, kerbos and pam, you can already :
– Join the domain
– Allowed user to connect on the linux pc to AD
– Manage Automatic Logon for web appli.
But it’s still have to work for
– Roaming profile
– Manage logon script (share folder and Printer)
Or maybe, it’s already done…. Just have to find it 🙂
Let me know.
@Smad [50]:
Hey, having left Novell, I’m not following AD integration so much any more. The features you request were known shortfalls in the feature set back when I wrote this. (I think that for a Linux client, they should be managed separately, anyway). Check samba.org for more info.
–Ted
I have used Active Directory on windows platform and i love the way it works and i have found it to be easy to understand while other may claim that its hard to understand!
Best Regards
This is just a nice article…..
I agree with the author that Microsoft Active Directory (MAD as we should call it) does a lot more than just an openldap type service would do because of the management capability and the tools for configuration.
Linux NEEDS a directory service to get anywhere in the corporate world.
But how about this as a different track, Having worked with NDS on Novell’s Netware in the past, it would be great if Novell would carry on down their open source route and start to open up the innards of NDS.
Having Linux integrate with MAD is one thing, but the other way to look at this is to have a native (NDS based?) Linux directory and have windows clients integrate. NDS has the advantage to my mind of always supporting more platforms than MAD, it has of course always has a windows emphasis, but I think it offers the most potential for a cross platform directory service.
Maybe some will think that we are too far down the MAD route, but one thing we can be sure of (and history bears this out) is that things change and often radically so, we need to be ready for this. For an organisation to commit to a Linux rollout wholeheartedly (and ditch windows), having an alternative and WORKABLE ds a vital factor.
Regards,
Andrew
We’ve been heading this way ever since LAN Manager2 was introduced in OS|2. I was one of the first to request OS|2 Domain compatibility for Samba. I am also quite familiar with Novell NDS, it is less than complete, IMHO.
I disagree with Andrew Stringer. The answer is not to come out with a different and incompatible DS standard. That will only assure Linux a permanent place in the tinkerware category. The winning strategy, used by Microsoft, against IBM, is to subvert and extend. This is why Sun was so quick to sue MS over their extended Java JVM. The MS JVM was a subvert and extend play and had MS succeeded, MS would have taken over Java in short order.
With the recent EC decisions, MS has to make the full AD schemes and functionality available to the public. Even MS cannot ignore multiple 2.6BUSD fines, which is the minimum of what the USDOJ should have done to them years ago.
That said, what you denigrate as MAD is actually a very nice system that subverts and extends known good standards (LDAP and Kerberos) for MS’ gains (customer retention). The NDS attempt was half-assed at best, in comparison. Neither was it any more open than AD. The subvert and extend approach works best when you do it to the market leader, not some distant also-ran.
Errata: The EC fines against Mickeysoft are in Euros, exceeding 2.6BEUR. They are recurring until MS complies. MS has used their last appeal.
NDS and edirectory, a brilliant system but it suffered from the problem the client was not native in Windows, they only ever supported Netware Bindery in win 3.1 and Win95 unless you installed the Netware client which in early versions was a memory hog. However it gave you powerful login scripts (NT really only let you run .bat files or supply your own script interpreter) and when integrated with Zenworks allowed policy management of Win95/NT/XP desktops from within one policy editor and later versions could even read custom policy editor files so anything in the registry could be set via policy. The problem was NDS and eDirectory did not run well in Windows early on and was difficult to configure well, so you had to have Netware for good support.
Now Gnome configures much of it’s environment with gconf which to me just looks like a registry. Why not extend policy to this?
Local profile – could it not be possible to create an app that can run before the users x session starts to rsync their ~ folder to a network location. Maybe have a simple config file structure to include or exclude specific files/folders. That’s all windows roaming profile is.
Gunther and Lars did a great job integrating this into SLED. If you’re running a non-SLED distro or want some additional functionality, you might want to check out Likewise Open (Disclaimer: I work for Likewise). Likewise Open is free, open source, software that accomplishes the same thing. If you want additional functionality, we also have a non-free, commercial product, Likewise Enterprise, that adds group policy and several other features.
@mvellon et al:
Cool tip. Thanks for letting readers know.
As a point of clarification, the work Guenther (now at Red Hat) and Lars did on this is all free software as well. They both did this work as part of the Samba team during the era that Jeremy Allison was still at Novell. The Samba team, as many readers will attest, are extremely passionate about Free Software.
The one critique that could be made is that the easy admin components shown are part of YaST, which is open source, but is used mainly/only by SUSE-based distributions.
To readers investigating Likewise Open, I make no recommendation for or against, but I do advise to make sure that Likewise Open is using the hooks in Samba in order to comply with how most distros would provide such Active Directory functionality.
Ted,
I know Guenther and Lars from their work on Samba. Jerry Carter (one of the other Samba 3 team members) is a Likewise employee and has done much to educate us on what it means to be an open source company.
As to Likewise Open, given its Samba connection, yes, it is fully Samba aware/compatible. You can do the AD “join” with Likewise and then set up Samba to be a member-server. We ship an “id mapper” that plugs into Samba to assure that it performs SID-id mapping in a consistent fashion. We also set up the Samba smb.conf file in a way to be compatible with the Likewise configuration file.
To simplify access control, I develop all of my company’s Intranet apps to use Active Directory pass-through authentication. This identifies the user and determines their access rights based on their AD group membership. The app then provides a 2nd hop, impersonated pass-through authentication to a SQL Server 2005 database. It’s completely transparent to the user when they hit one of my apps, appearing to magically know who and where they are.
I haven’t seen a Linux-based web browser that is capable of reliably handling AD pass-through authentication. Is a “plug-in” or hack available that can provide this functionality? If so, I could potentially recommend a Linux-based PC deployment to some of our temporary job sites to assist in detering PC theft and misuse on corporate time.
@DVS:
You asked, “I haven’t seen a Linux-based web browser that is capable of reliably handling AD pass-through authentication. Is a ‘plug-in’ or hack available that can provide this functionality?”
When Lars and first demonstrated this to me, they showed it using a SUSE Linux system with Firefox. If I remember correctly, they told me that Firefox on SUSE is natively Kerberized, so pass-through authentication to OWA worked without a hitch. That’s going from distant memory at this point, so you’ll need to test to verify.
–Ted
[…] este blog un trabajador de Suse cuenta el magnífico trabajo de integración que están haciendo para que un […]
Hi,
I ve a question. I ve over 20 computers in a lab and i want to control those pc; by creating group policy, managing the network, giving access or not to web-sites, and keep logs of all the computers and something like that.. with the a linux based server. How can i do that or can i do that? And that must be free. I can not pay cost.
Thank you from now
Johaqin
@Johaqin: I recommend starting at Samba.org to find out the latest.